Microsoft SharePoint Zero-Day Hack Hit ‘Thousands of Server Thousands’
A zero-day vulnerability in Microsoft’s Sharepoint Server Software has triggered a global cyber attack affecting the government and commercial network. Tens of thousands of servers are at risk, no complete fixed yet.
Listen to the story

In short
- Zero-day Sharepoint Dosha was exploited in global cyber attack
- Two version of Sharepoint were patches, one is yet to be decided
- Hackers can maintain access even after patching
A new discovered vulnerability in Microsoft Sharepoint has led to a comprehensive cyber attack, which compromises servers in government agencies, businesses and universities around the world. The so-called “zero-day” exploitation, which targets already unknown defects, has influenced thousands of on-primeses Sharepoint servers in many countries, motivating immediate security alerts and investigation. Microsoft confirmed the violation in a security advisor issued on Saturday, warning of “active attacks” and urged immediate implementation of protective measures. “This is an important vulnerability,” Adam Mayors said, Senior Vice President of Cybercity Firm Crowdastric. “Any person hosted Sharepoint server has a problem.”
While Microsoft has released a patch for two versions of the software, fixed for a version, Sharepoint 2016, is still being developed.
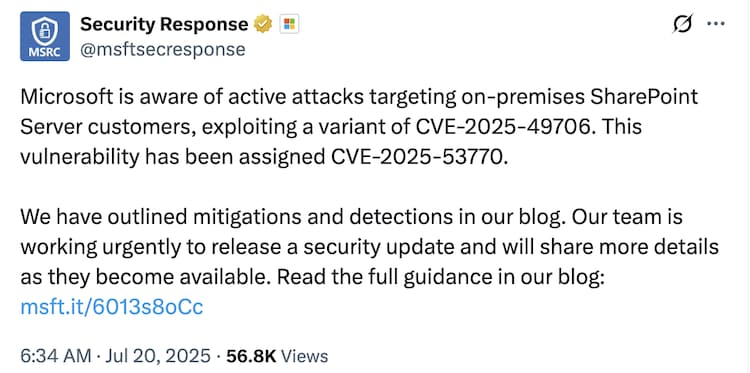
Microsoft has released a safety patches for SharePoint Subscription Edition and Sharepoint 2019, after active exploitation of a significant vulnerability, was tracked as CVE-2025-537770, in on-primesies servers. The tech veteran confirmed that the defect is currently being targeted in the wild and urging customers to apply the update immediately.
The vulnerability does not affect Sharepoint online, Microsoft said in a tweet through its safety response center (MSRC) handle on Sunday. However, on-dimases server are at risk, especially those who run those who run.
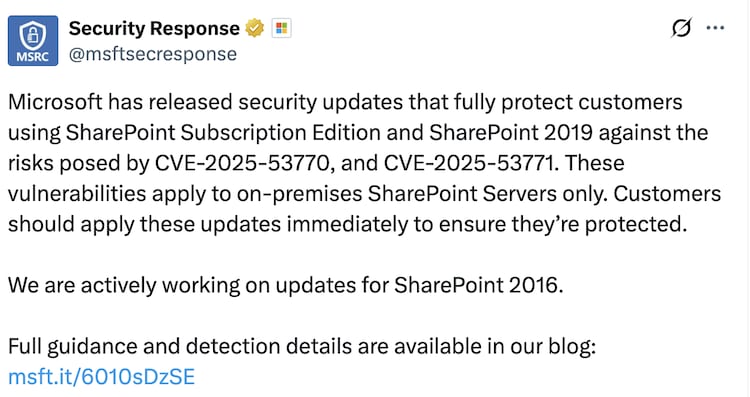
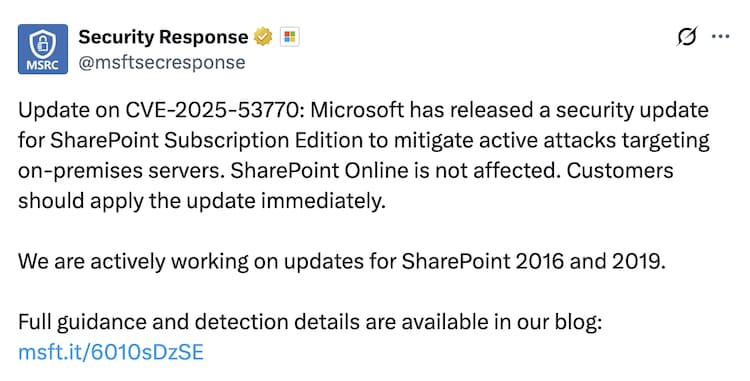
Microsoft said, “We are actively working on updates for Sharepoint 2016 and 2019,” the company has also provided guidance and mitigation to the defenders available through its official blog.
SharePoint does not affect users within the cloud atmosphere of Breach Microsoft 365. Instead, it targets the internal server hosted within organizations – usually used for sharing and cooperation by government bodies and large enterprises.
As Washington Post, Who first reported the incident, hackers managed to take advantage of the defect in recent times, gained access to American federal and state agencies, European governments, energy firms, a university in Brazil and an Asian telecom company. In some cases, the attackers “abducted” the public document repository, stopping the authorities from accessing them.
Rentally, the vulnerability allows for a type of spuofing attack, where an intruder can disguise itself as a reliable source. With access to Sharepoint server, which is often associated with services such as outlook and teams, hackers can steal sensitive data, harvest passwords, and potentially maintain long -term access to using cryptographic keys.
According to reports, what is especially related to, it is that the attackers have received access keys that can allow them to return even after the system is patched. “Pushing a patch out on Monday or Tuesday does not help anyone, which has been compromised in the last 72 hours,” said a security researcher. Washington Post.
Any technical details of the exploitation chain have not been publicly disclosed yet, but the confirmation of Microsoft’s active attacks suggests that vulnerability may be part of a target campaign. The company’s advisor underlines the urgency of implementing the fix, especially for the enterprise systems that rely on Sharepoint for cooperation and material management. Microsoft is expected to release patch for Sharepoint 2016 and 2019 soon, but till then, system administrators are advised to monitor unusual activity and follow the stages of detection mentioned under the guidance of Microsoft.