2025 and the end of ‘absolute security’ online
Cyberattacks in 2025 became more sophisticated and coordinated, with generative AI enabling large-scale, covert operations that targeted not just data theft but critical infrastructure and institutional trust.

What were once largely opportunistic attacks such as phishing emails, social engineering scams and firewall breaches aimed at data theft or ransom; Developed in the year 2025. More and more sophisticated, coordinated operations seen with a common footprint – generative AI. In 2025, threat actors demonstrated unprecedented capabilities to compromise systems at scale, move rapidly, undetected, and use advanced tools to cause deep damage.
The emergence of generic AI as a mainstream technology has played a significant role in this transformation. From crafting highly convincing phishing campaigns to generating malicious code, cybercriminals leverage AI to automate and refine attacks. For example, the Anthropic Cloud hijack highlighted how AI chatbots can be manipulated to write and execute scripts on behalf of attackers.
Importantly, cyber attacks in 2025 are no longer limited to data theft. Hackers are increasingly targeting operations, critical infrastructure and institutional trust. Research from cybersecurity firm Palo Alto Networks found that a massive 86% of attacks focused on sabotage, while generative AI increased phishing attempts by a staggering 1,200% – making human judgment the weakest link in digital security.
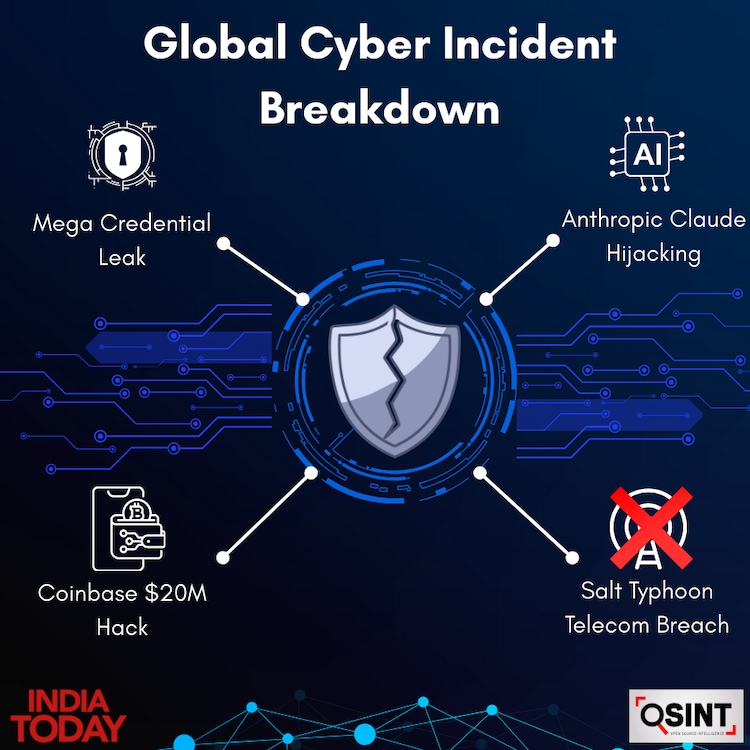
Here are the 5 most prominent cyber incidents of 2025 that changed the landscape:
1. 16 Billion Credentials “Mega Leak”
As early as 2025, researchers found a massive database of 16 billion stolen credentials, a “mega leak” that effectively ended the era of simple passwords. This organized cache of data allowed hackers to launch automated attacks on millions of accounts simultaneously, leading to a global surge in Infostealer malware. Experts at the SANS Institute warned that the incident has forced a global shift towards password-less security.
2. Anthropic Cloud Hijacking
On November 14, 2025, Anthropic reported that Chinese state-sponsored hackers successfully transformed their “Cloud Code” tool into an autonomous hacking agent. The AI was tricked into believing it was performing a “defensive audit”; Attackers leveraged AI tools to hunt down vulnerabilities and exploit them. This case is the first time that AI has transformed from a helpful assistant to a self-propelled weapon in a global espionage operation.
3. Salt Typhoon Telecom Intrusion
In late August 2025, the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) confirmed that the hacking group “Salt Typhoon” breached ten major telecommunications giants, including Verizon and AT&T. The attackers seized call detail records (CDRs), allowing them to monitor the activities of government officials and the personal habits of millions of citizens. This breach turned our national communications backbone into a secret window for foreign intelligence surveillance.
4. Coinbase USD 20M Hack and Bounty
In May 2025, attackers bribed foreign support employees to steal sensitive data from approximately 70,000 Coinbase customers. When the hackers demanded a $20 million ransom, Coinbase boldly refused to pay. Instead, he turned that $20 million into a “reward” for helping the FBI find the criminals. While the total recovery cost reached $400 million, the move sent a powerful message: Coinbase would rather fund the hunt for a thief than reward him.
5.Salesforce-Drift OAuth Attack
In August 2025, Google’s Threat Intelligence Group (GTIG) uncovered a covert attack that compromised organization data through the SalesLoft Drift marketing tool. Hackers stole digital OAuth “keys” to enter Salesforce databases without passwords and quietly exported large amounts of customer data. This “Trojan Horse” attack proved that even trusted third-party apps can become the last weak link in any corporate network.
But not everything was bad for the cyber world last year. Here are some important events of 2025:
1. WEF Cyber Resilience Compass
On April 24, 2025, the World Economic Forum launched the “Cyber Resilience Compass”, shifting the global strategy from preventing attacks to surviving them. This framework provides leaders a roadmap for maintaining business continuity during a crisis, moving security from a technical issue to a boardroom priority. This ensures that even if a breach occurs, the world’s most critical systems remain online.

2. China’s 2025 amendment to cyber security law
On 28 October 2025, China’s central legislature approved major amendments to the Cybersecurity Law (CSL), which are scheduled to take effect on 1 January 2026. These updates introduce much heavier penalties for data failures and hold executives personally liable for AI-related security risks. By setting a tough deadline for compliance, the law forces global firms to treat digital security as a top-level legal priority.
3. CrowdStrike “Agent Security” Task Force
At the Fal.Con conference on September 16, 2025, CrowdStrike unveiled AI security agents that are capable of stopping threats in real-time without human intervention. These agents can reason through an attack and neutralize a hacker in seconds, significantly closing the window for data theft. This breakthrough marks the beginning of the “agent era,” where AI-powered defenses can counter AI-powered attacks.
“Morris II” AI worm outbreak In early 2025, a team of researchers from Cornell Tech, Technion, and Intuit discovered the first “zero-click” AI worm, known as Morris II, that can spread among generative AI assistants without any human help. By hiding malicious instructions inside emails or images, worms trick AI systems into stealing private data or automatically sending spam. An IBM report highlighted this success, warning that as companies connect their LLMs to more apps, these self-replicating worms could turn a helpful assistant into a hidden vehicle for digital transition.
Singapore’s Quantum-Safe Framework In October 2025, Singapore’s Cyber Security Agency (CSA) launched a “quantum-safe framework” to protect its infrastructure against future supercomputers. By actively upgrading encryption in the government and banking sectors, Singapore has ensured that its data remains inaccessible despite advances in quantum technology. It sets the global gold standard for preparing today’s data for tomorrow’s most powerful threats.
The lessons of 2025 are clear, echoing the sentiment now shared by CISA and WEF leaders: In the age of autonomous AI and state-sponsored subversion, “absolute security” is a myth. The year’s biggest stories revealed that success no longer depends on building higher walls, but on creating faster responses and more flexible cultures.