Black Friday scam alert: Over 2,000 fake brand websites discovered, including Amazon lookalike
The Black Friday sale is live around the world, with huge discounts being offered on smartphones and other electronics. But be careful, with the sale on the way, cyber criminals have launched thousands of fake online stores to exploit buyers. This large-scale scam jeopardizes consumer data security and e-commerce trust during the peak shopping season.

If you’re looking for that discounted iPhone 17, a shiny new pair of Ray-Bans, or a half-price smartwatch this Black Friday sale, you might want to think twice before clicking “Buy Now.” While genuine deals are flooding the internet, cyber criminals are busy weaving a wide web of scams to cash in on the shopping frenzy. CloudSEEK, a cybersecurity firm, issued a dire warning after uncovering more than 2,000 fake, holiday-themed online stores imitating top retail brands like Amazon, Samsung, Apple, and Jo Malone. Target? Stealing personal data and payment information from buyers eager to score a deal.
Black Friday scam: what’s happening?
According to the latest report from CloudSEK, cybercriminals are operating one of the largest and most sophisticated phishing ecosystems seen in recent years. These fake sites are designed to look identical to real online stores with festive banners, countdown clocks, fake trust badges, and pop-ups showing “recent purchases,” all engineered to create a false sense of urgency.
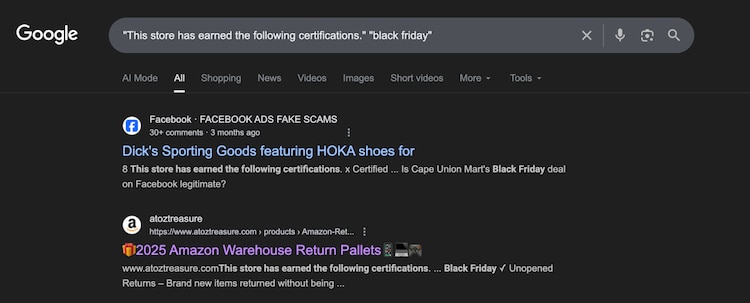
The report shares complete research on these scams and explains every step of what is happening. According to this, once users proceed to checkout, their information is silently collected and redirected through the attacker-controlled payment portal, enabling financial theft with alarming efficiency.
The report called this development a “shift from sporadic scams to industrial-scale fraud”. The researcher behind the report warned that, without quick intervention, these operations could “cause significant harm to consumers and reduce confidence in e-commerce during the busiest shopping period of the year.”
CloudSEK analysts say the scam network is being augmented by short-term social media advertisements, search engine manipulation and even links circulated through WhatsApp and Telegram groups. This means that unsuspecting users may stumble upon fraudulent stores even before they reach legitimate brand sites.
The company estimates that each fake store attracts hundreds of visitors in a short period of time, and between 3 percent and 8 percent of them convert into victims. At that rate, scammers could make between $2,000 and $12,000 per site before the fraudulent domains were removed.
scam groups
CloudSEK’s investigation identified two large clusters of interconnected phishing websites. Cluster One contains over 750 linked domains, including over 170 Amazon-themed lookalike names that mimic legitimate URLs. These sites use similar templates, flashing discounts, and fake social proof to lure victims. Many of them also load resources associated with previous malware campaigns, suggesting that the same operators are behind multiple fraud schemes.
Cluster two is even larger, consisting of over 1,000 domains registered under the .shop extension. These sites impersonate popular brands using a standardized Black Friday or Cyber Monday layout. The report said, “The second cluster spans a broader .shop ecosystem and includes domains that appear to mimic well-known consumer brands – such as Apple, AMD, Dell, Cisco, Logitech, Toshiba, Ray-Ban, Nivea Men, paula’s Choice, Rare Beauty, SK Hynix, 8BitDo, Viomi, Tim Hortons, Aetna, Ahava, Olympus, Snapple, Fio, GoTrax, Meetian, Yale, Xiaomi, Jo Malone, Fujifilm, Amazfit, COSRX, Samsung, Garmin, Shark, HP, Seagate and Omron – based on naming patterns and shared template attributes.”
CloudSEK researchers believe this cluster was created using mass-produced phishing kits, allowing scammers to open a large number of fake stores with minimal effort. “These are not isolated hackers, but part of a broader fraud ecosystem,” the report said. The report details how criminal groups are reusing templates, graphics and scripts to deploy cloned websites within hours.
Its impact extends far beyond the stolen money. Victims also suffer identity theft and long-term data misuse, while legitimate brands suffer reputational damage, higher support costs and lost revenue as buyers migrate to fake sites.
How to stay safe this holiday season?
CloudSEEK and other cybersecurity experts are urging shoppers to be extra vigilant during this year’s Black Friday and Cyber Monday sales. Warning signs of a scam site include:
- Unrealistic discount of 70-90 percent
- Countdown timer or instant “last few left” pop-ups
- Misspelled or unusual URLs that are slightly different from the official domain
- Fake Trust Seal or Unverified Certificate
- Checkout pages that redirect to unfamiliar sites
- Recycled layouts used across multiple “brands”
- No verifiable customer support contact information
Experts recommend that the safest way to purchase is through official brand websites, verified apps or trusted marketplaces like Amazon or Flipkart.
CloudSEEK also called on retailers and regulators to take proactive steps, including monitoring new domain registrations, tracking impersonation attempts, and setting up rapid takedown systems. For governments and cybersecurity agencies, the report recommends collaboration across sectors to dismantle coordinated phishing networks and work with advertising platforms to stop the spread of scam campaigns.
Vigilance is key, the report says, “The scale of these scams shows that cybercriminals are evolving as rapidly as online shoppers. Awareness is the first line of defense.” So before you rush out to grab that “too-good-to-be-true” deal this Black Friday, take a moment to double-check the site. Because in the shopping season of 2025, not every checkout is what it seems.